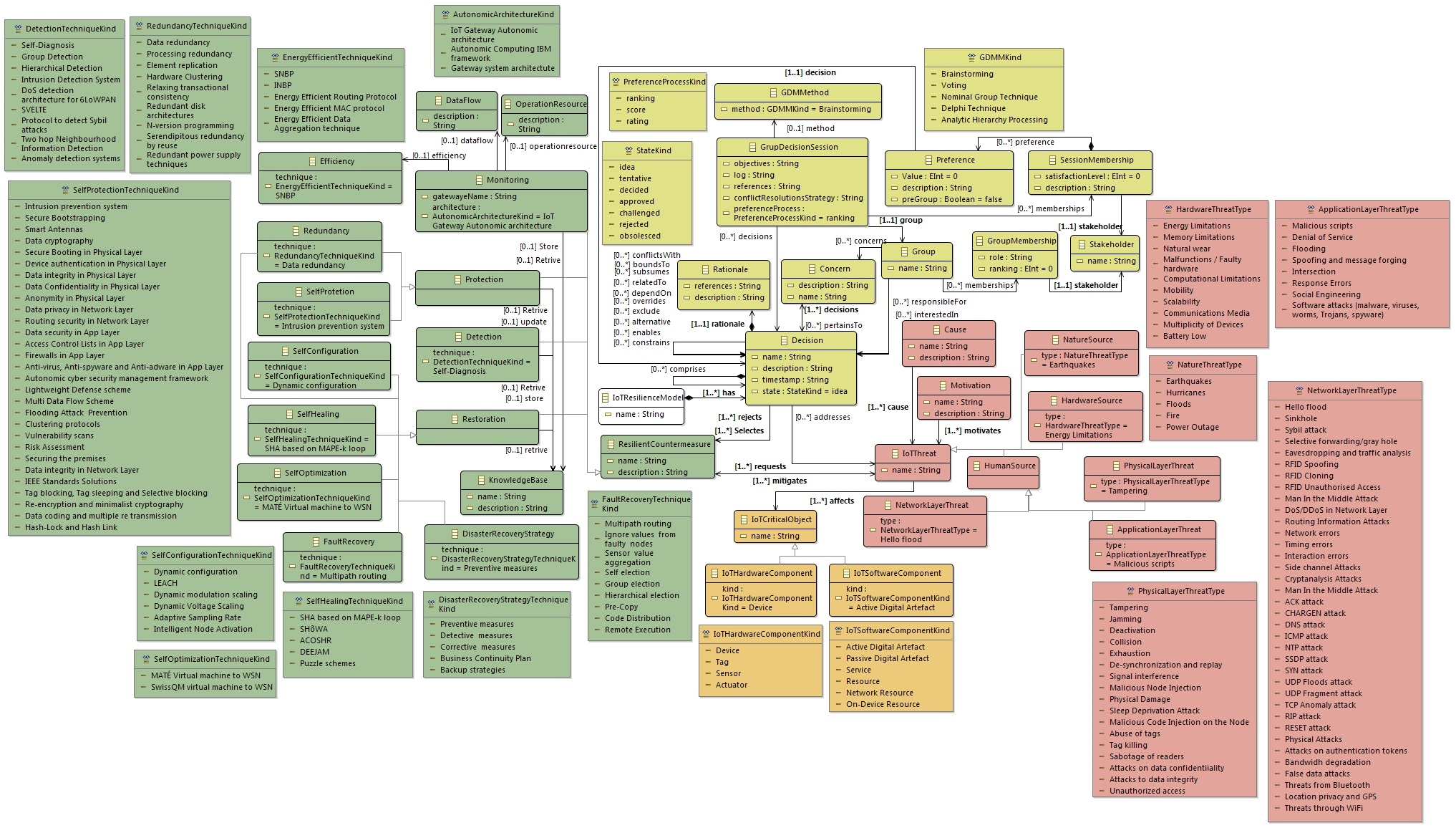
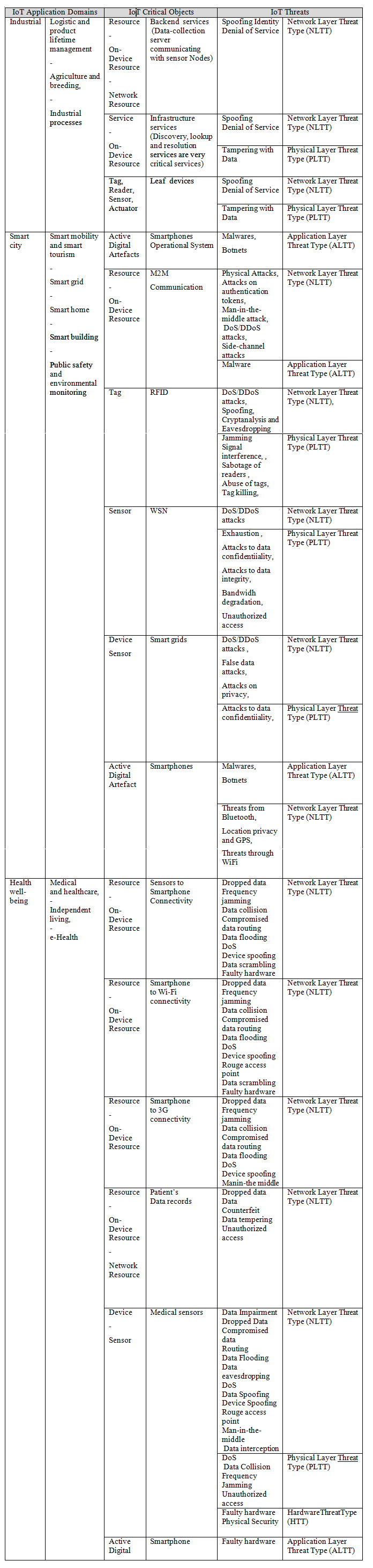
Identify IoT Threats and IoT Critical Objects in An IoT Application Domain using
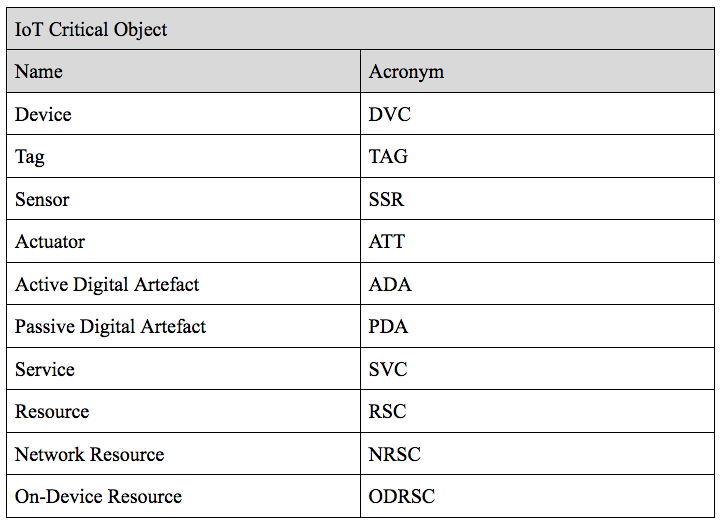
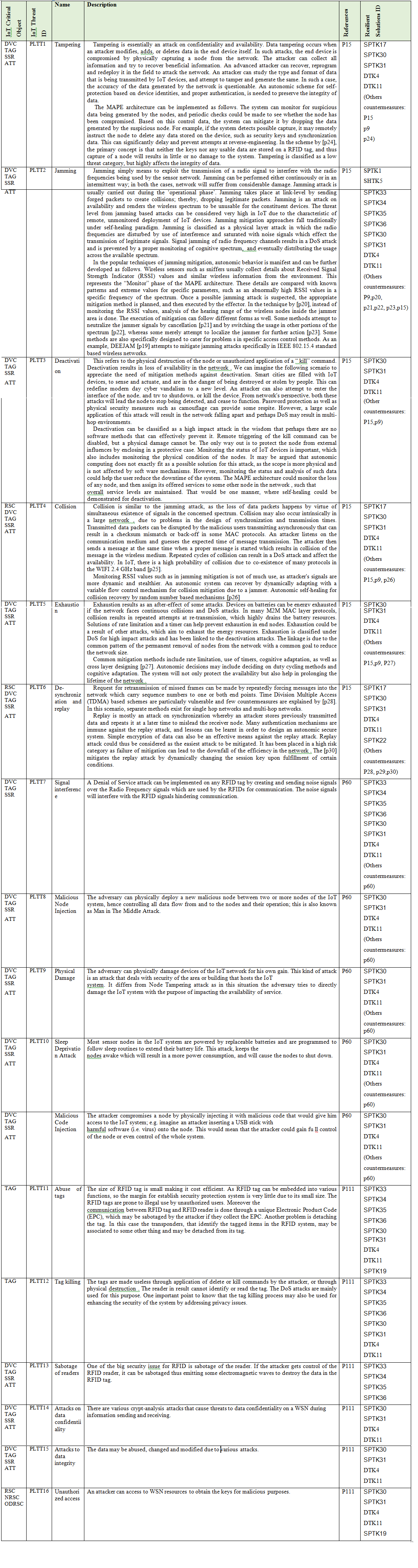
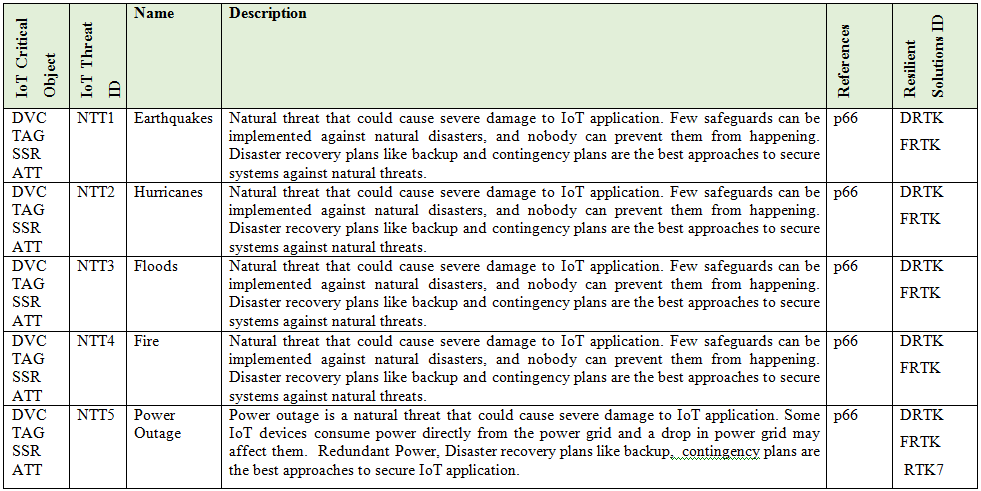
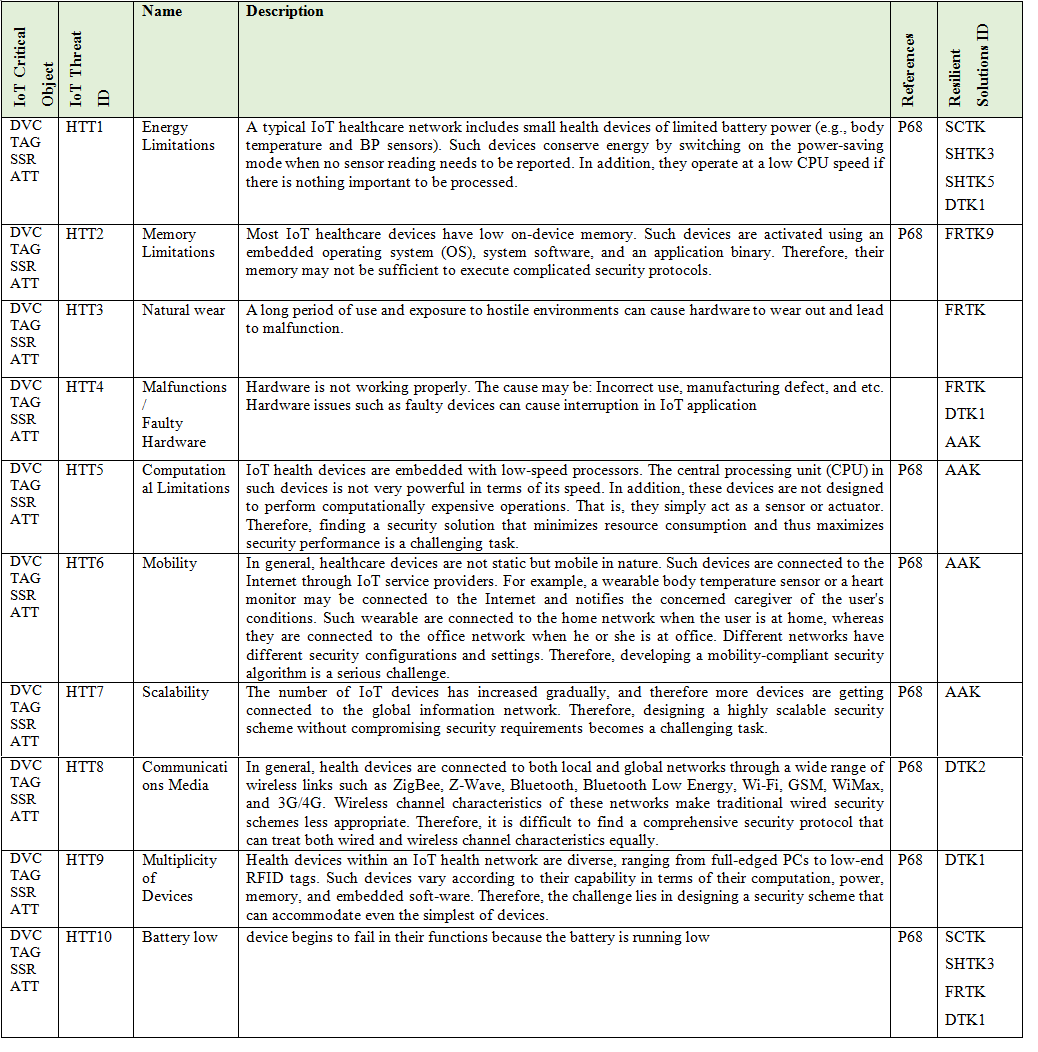
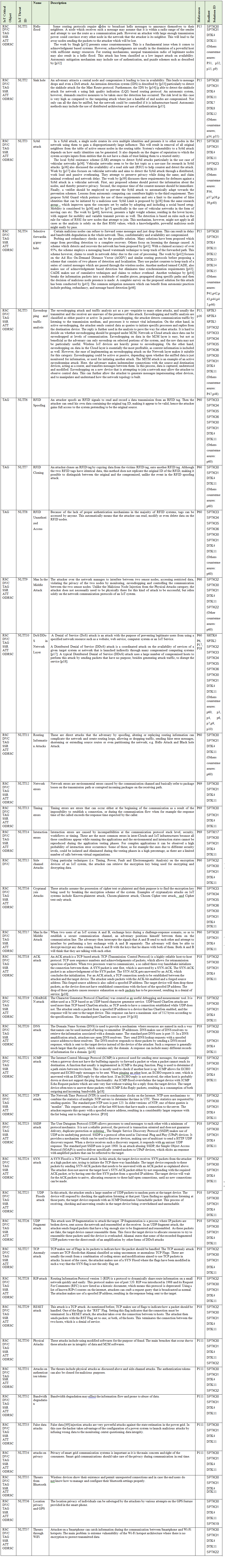
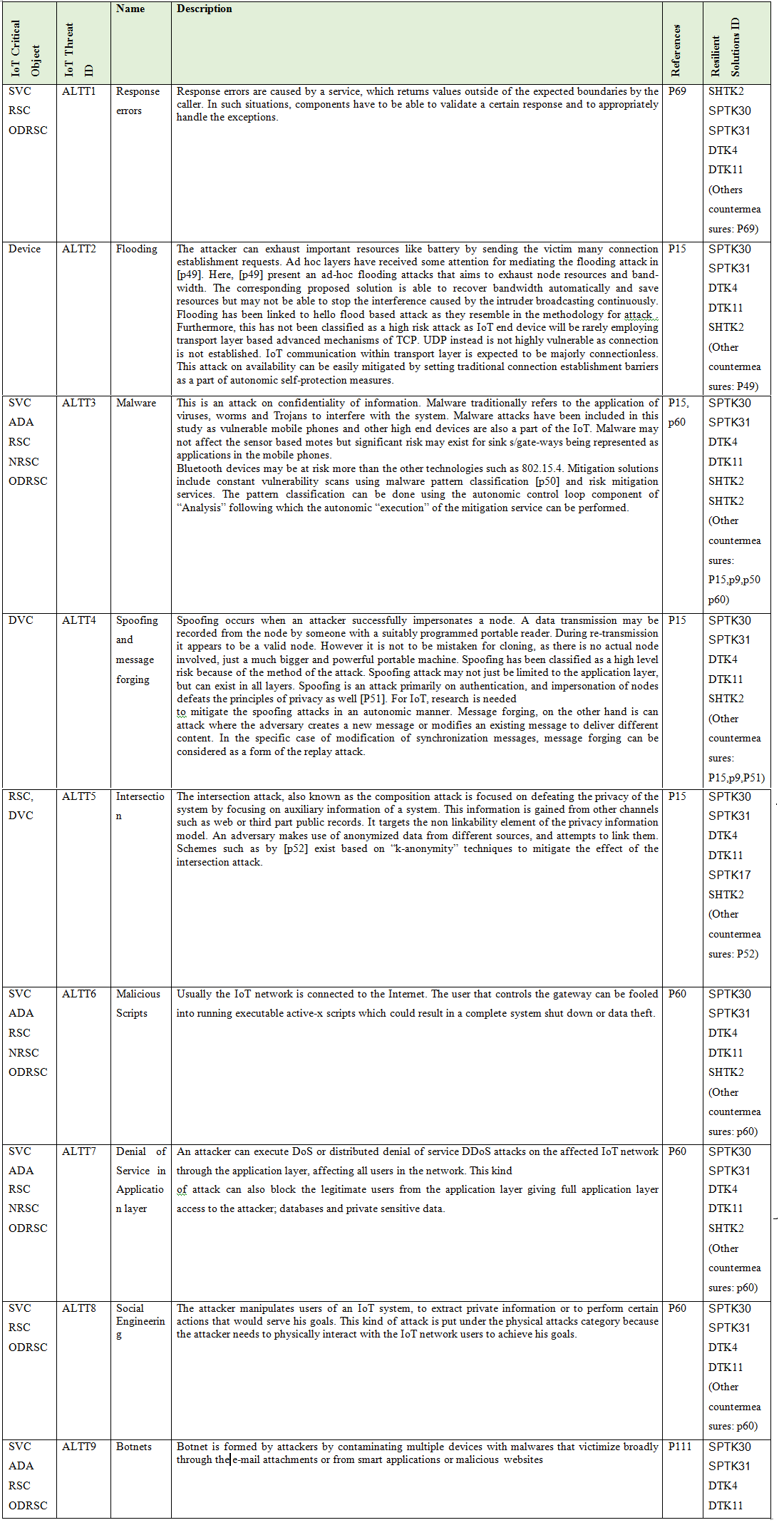
Here we present the main IoT Critical Objects and the possible IoT Threats. These IoT Threats correspond to the Enumeration that composed the ADDM4RIOTA and are presented in detail in the tables: Table 1 - Physical Layer Threat Type (PLTT), Table 2 -Nature Threat Type (NTT), Table 3 - Hardware Threat Type (HTT), Table 4 - Network Layer Threat Type (NLTT), Table 5 - Application Layer Threat Type (ALTT).
For a more detailed description of how to use ADDM4RIOTA and the tables (enumerations) see Modeling Process.
p1 - Self-management in Internet of Things - Timo T¨ oyry
p2 - Introducing Autonomy in Internet of Things
p3 - Detecting Distributed Denial of Service Attacks Using Data Mining Techniques
p4 - Methodologies for detecting DoS/DDoS attacks against network servers
p5 - Detecting DoS and DDoS Attacks by using an Intrusion Detection and Remote Prevention System
p6 - Denial-of-Service detection in 6LoWPAN based Internet of Things
p7 - Denial of Service Attacks in Wireless Networks: The Case of Jammers
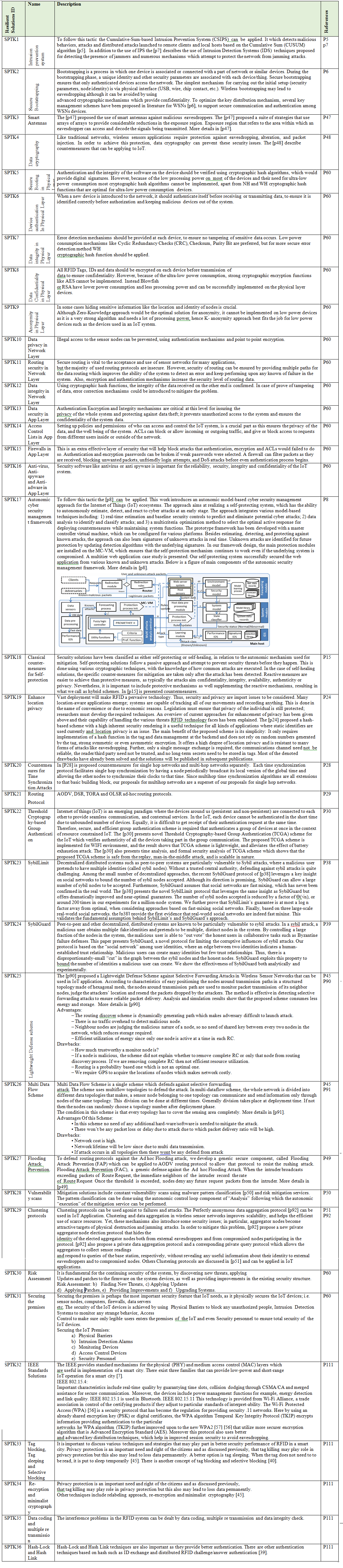
p8 - A Model-Based Validated Autonomic Approach to Self-Protect Computing Systems
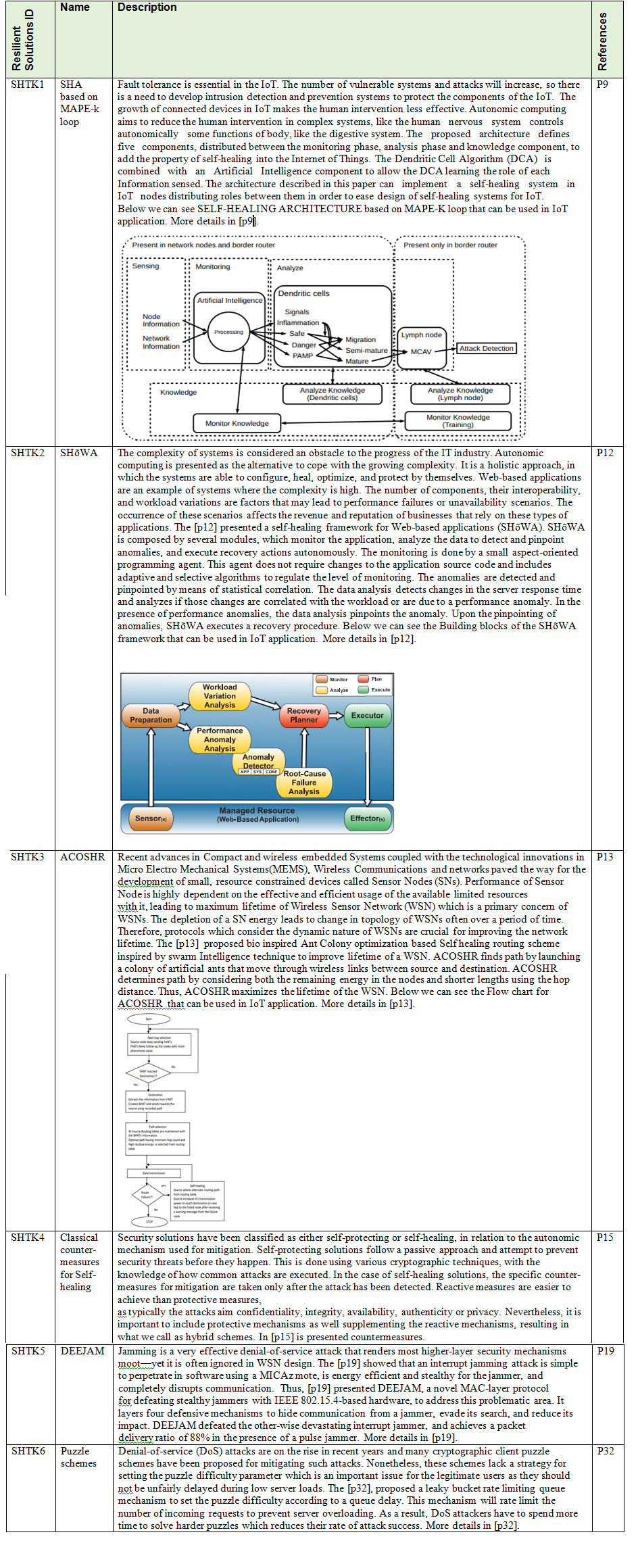
p9 - An Architecture for Self-healing in Internet of Things
p10 - SVELTE: Real-time intrusion detection in the Internet of Things
p11 - Energy-Efficient Communication Protocol for Wireless Microsensor Networks
p12 - SHoWA : A Self-Healing Framework for Web-Based Applications
p13 - Bio-Inspired Self-Healing Routing to Improve Lifetime of Wireless Sensor Networks
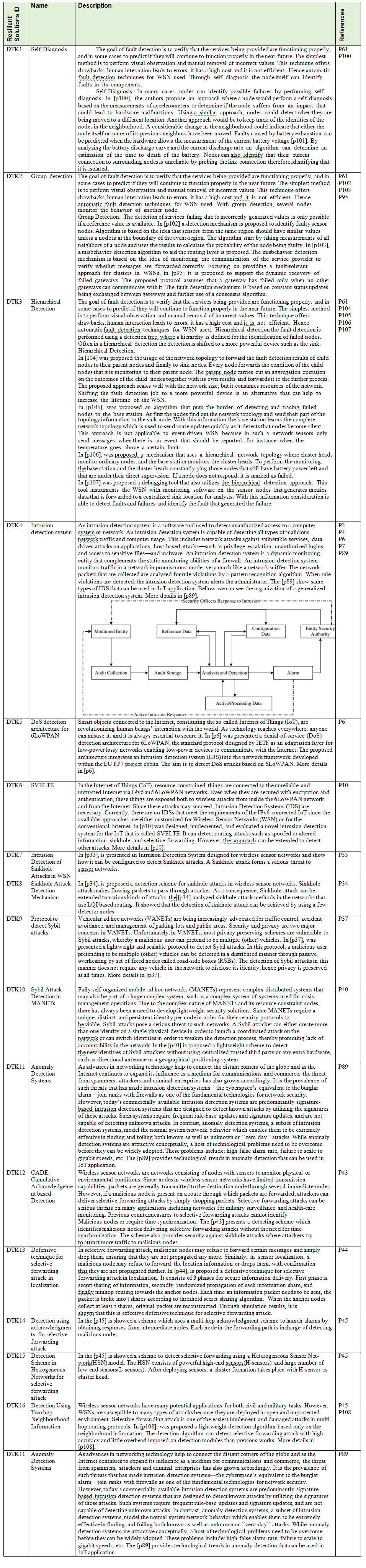
p14 - Autonomic Protocol and Architecture for Devices in Internet of Things
p15 - Autonomic schemes for threat mitigation in Internet of Things
p16 - On the features and challenges of security and privacy in distributed internet of things
p17 - Distributed Denial of Service: Taxonomies of Attacks, Tools and Countermeasures
p18 DDoS through the Internet of Things
p19 - DEEJAM: Defeating Energy-Efficient Jamming in IEEE 802.15.4-based Wireless Networks
p20 - Wireless Jamming Localization by Exploiting Nodes’ Hearing Ranges
p21 - Design and implementation of spectrally-encoded spread-time CDMA transceiver
p22 - A Survey of Security Mechanisms with Direct Sequence SpreadSpectrum Signals
p23 - Joint reactive jammer detection and localization in an enterprise WiFi network
p24 - Tackling Security and Privacy Issues in Radio Frequency Identification Devices
p25 - IEEE 802.15.4 Low Rate –Wireless Personal Area Network Coexistence Issues
p26 - RFID Reader Receivers for Physical Layer Collision Recovery
p27 - A survey of energy-efficient wireless communications.
p28 - Time synchronisation attacks in sensor networks.
p29 - Mobile ad hoc networking (MANET): routing protocol performance issues and evaluation considerations
p30 - Threshold Cryptography-based Group Authentication (TCGA) Scheme for the Internet of Things (IoT)
p31 - Hello Flood Attack and its Countermeasures in Wireless Sensor Networks
p32 - Rate Limiting Client Puzzle Schemes for Denial-of-Service Mitigation
p33 - Intrusion detection of sinkhole attacks in wireless sensor networks
p34 - A Sinkhole Attack Detection Mechanism for LQI based Mesh Routing in WSN
p35 - Detection and mitigation of sinkhole attacks in wireless sensor networks
p36 - LSR: Mitigating Zero-Day Sybil Vulnerability in Privacy-Preserving Vehicular Peer-to-Peer Networks
p37 - P2 DAP – Sybil Attacks Detection in Vehicular Ad Hoc Networks
p38 - SybilLimit: A Near-Optimal Social Network Defense against Sybil Attacks
p39 - SybilGuard: Defending Against Sybil Attacks via Social Networks
p40 - Lightweight Sybil Attack Detection in MANETs
p41 - Selective forwarding attack detection using watermark in WSNs
p42 - Defending selective forwarding attacks in WMNs
p 43 - CADE: Cumulative Acknowledgement based Detection of Selective Forwarding Attacks in Wireless Sensor Networks
p 44 - Secure Localization with Defense Against Selective Forwarding Attacks in Wireless Sensor Networks
p45 - A Survey On Selective Forwarding Attack in Wireless Sensor Networks
p46 - A survey on mitigation methods to Black hole Attack on AODV routing protocol
p47 - Securing Wireless Data Networks against Eavesdropping Using Smart Antennas
p48 - Overview of Security Issues in Wireless Sensor Networks
p49 - Flooding attack and defence in Ad hoc network
p50 - Toward an Automatic, Online Behavioral Malware Classification System
p51 - Secure and reliable clustering in wireless sensor networks: A critical survey
p52 - ACHIEVING k-ANONYMITY PRIVACY PROTECTION USING GENERALIZATION AND SUPPRESSION
p53 - Security Challenges in the IP-based Internet of Things
p54 - Internet key exchange (IKEv2) protocol. RFC 4306
p55- The transport layer security (TLS) p rotocol version 1.2. RFC 5246
p56 - Datagram transport layer security (DTLS) over the datagram congestion control protocol (DCCP). RFC 5238
p57 - Host identity protocol. RFC 5201
p58 - Protocol for carrying authentication for n etwork access ( PANA). RFC 5191
p59 - Extensible authentication protocol (EAP). RFC 3748
p60 - Internet of Things - Security Vulnerabilities and Challenges
p61 - Review on Fault Detection and Recovery in WSN
p62 - Security in Internet of Things: Challenges, Solutions and Future Directions
p63 - Internet of Things Security: Layered classification of attacks and possible Countermeasures
p64 - DEPENDABILITY AND ITS THREATS: A TAXONOMY (
p para usar na definição de threats)
p65 - Basic Concepts and Taxonomy of Dependable and Secure Computing (
p para usar na definição de threats)
p66 - Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intrudersand Attacks
p67: A new approach to investigate IoT threats based on a four layer model
p68: The Internet of Things for Health Care: A Comprehensive Survey
p69: Energy-Efficient and Fault Tolerant Methods for Message Delivery in Internet of Things
p70 - Energy Efficient Naive Bayes Prediction Model for Data Reduction in WSN
p71 - Data Reduction using Incremental Naïve Bayes Prediction (INBP) in WSN
p72 - Routing Techniques in Wireless Sensor Networks: A Survey
p73 - MAC Protocols for Wireless Sensor Networks: A Survey
p74 - Energy Efficient Reliable Data Aggregation Technique for Wireless Sensor Networks
p75 - Internet of Things: Wireless Sensor Networks
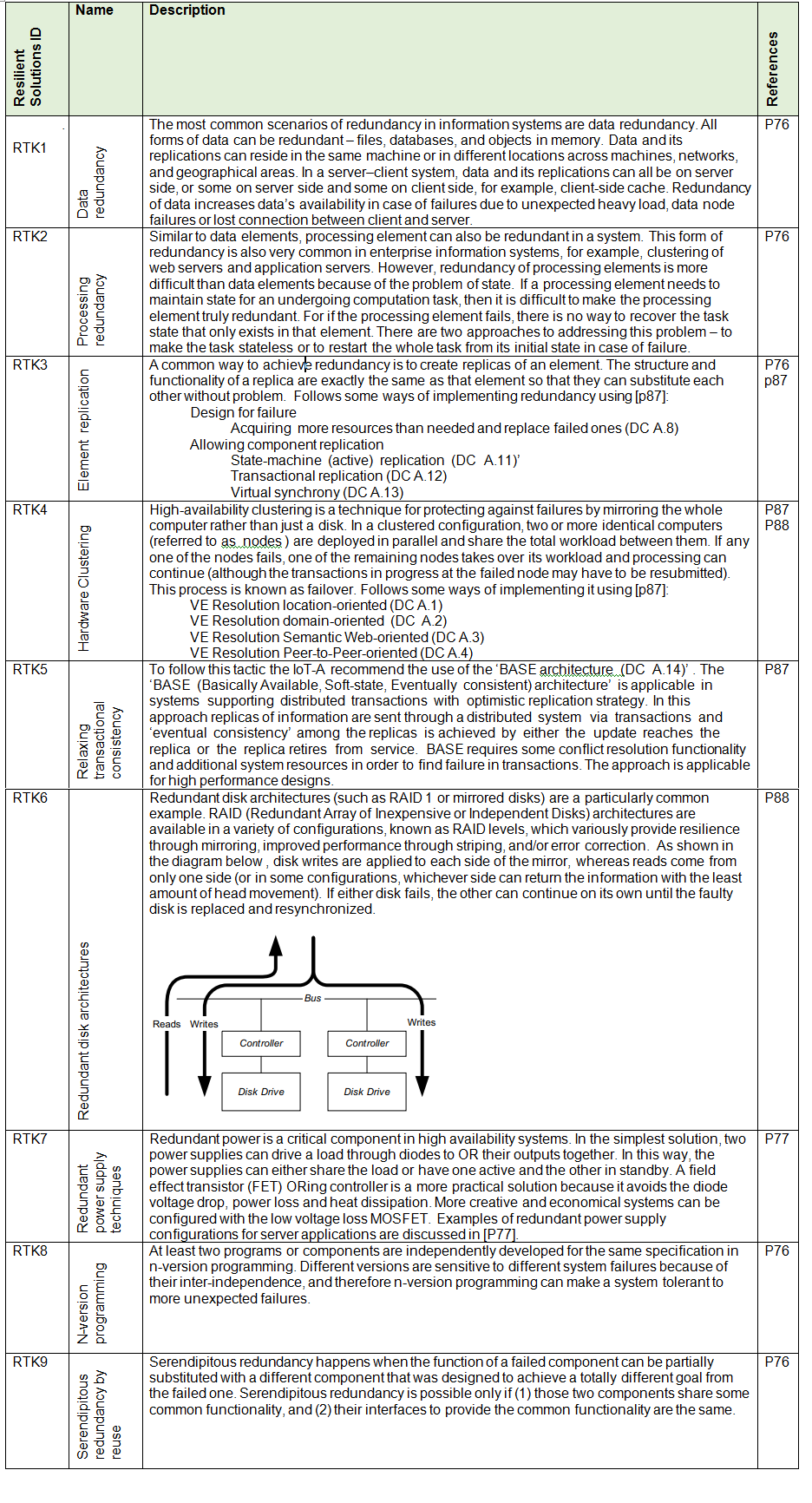
p76 - Architectural design for resilience
p77 - Redundant power techniques for servers explained
p78 - Advanced Low Energy Adaptive Clustering Hierarchy
p79 - DYNAMIC RECONFIGURATION TECHNIQUES FOR WIRELESS SENSOR NETWORKS
p80 - Adaptive Sampling Mechanisms in Sensor Networks
p81 - Random Coverage with Guaranteed Connectivity: Joint Scheduling for Wireless Sensor Networks
p82 - Design of Gateway for Monitoring System in IoT Networks
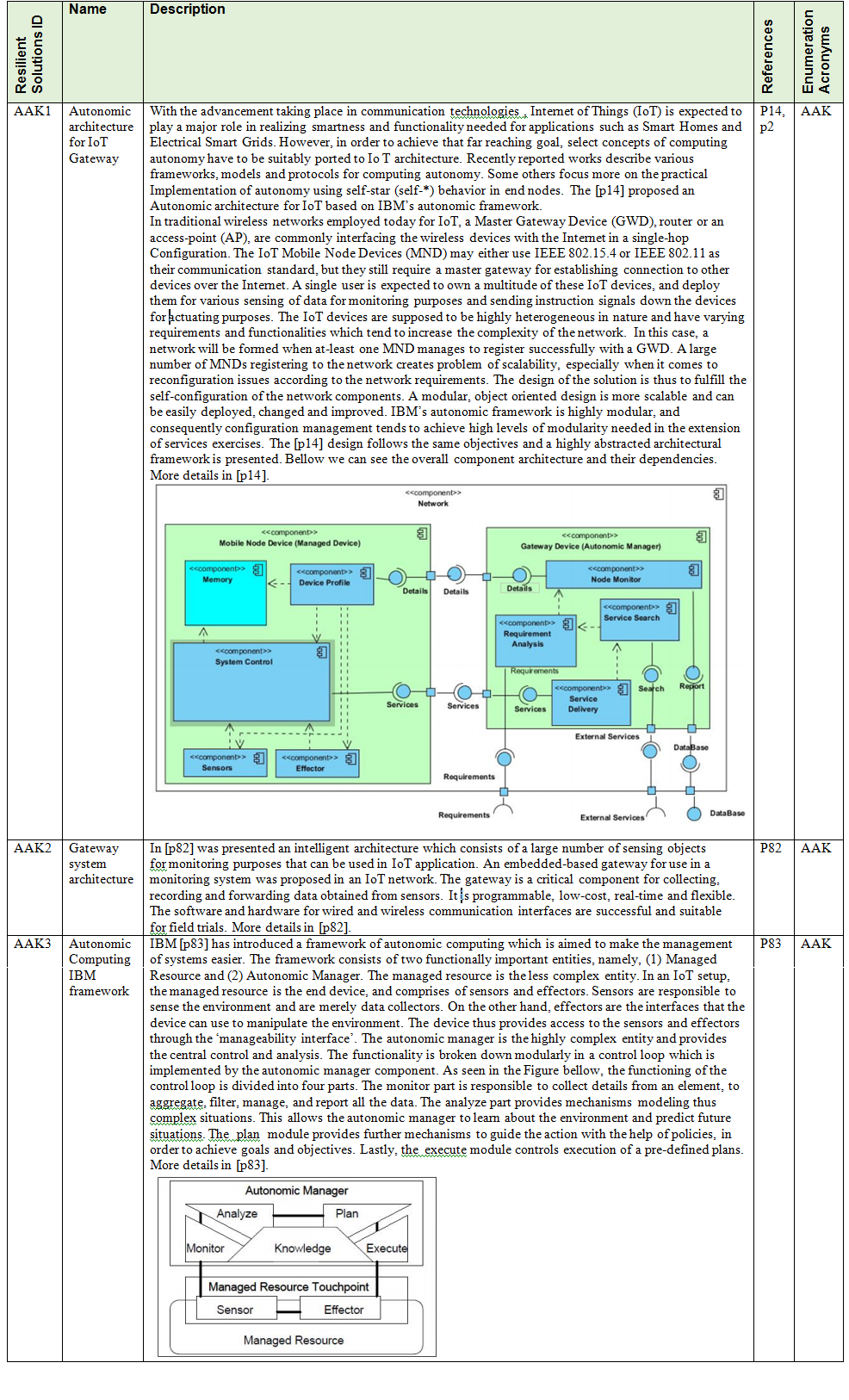
p83 - The vision of autonomic computing (IBM)
p84 - A Model Driven Engineering approach for Business Continuity Management in e-Health Systems
p85 – http://typesofbackup.com/backup-strategy-or-backup-policy/
p86 - https://technet.microsoft.com/en-us/library/cc938511.aspx
p87 – IoT-A
p88 – Software systems architecture: working with stakeholders using viewpoints and perspectives
p89 - An overview of anomaly detection techniques: Existing solutions and latest technological trends
p90 - Lightweight Defense Scheme against Selective Forwarding Attacks in Wireless Sensor Networks
p91 - An efficient countermeasure to the selective forwarding attack in wireless sensor networks.
p92 - Perfectly Anonymous Data Aggregation in Wireless Sensor Networks
p93 - Deploying Sensor Networks with Guaranteed Capacity and Fault Tolerance
p94 - Energy-Efficient Communication Protocol for Wireless Microsensor Networks.
p95 - Fault-Tolerant Clustering of Wireless Sensor Networks
p96 - Algorithms for Generic Role Assignment in Wireless Sensor Networks.
p97 - Maté: A Tiny Virtual Machine for Sensor Networks
p98 - The Remote Processing Framework for Portable Computer Power Saving
p99 - A Virtual Machine For Sensor Networks
p100 - Fault Tolerance in Sensor Networks Using Self-Diagnosing Sensor Nodes
p101 - Fault Tolerance in Wireless Sensor Networks – A Survey
p102 - Distributed Bayesian Algorithms for Fault-Tolerant Event Region Detection in Wireless Sensor Networks
p103 - Mitigating Routing Misbehavior in Mobile Ad hoc Networks
p104 - A Health Monitoring System for Wireless Sensor Networks
p105 - Efficient Tracing of Failed Nodes in Sensor Networks
p106 - Fault Management in Eventdriven Wireless Sensor Networks
p107 - Sympathy: a debugging system for sensor networks.
p108 - Detecting Selective Forwarding Attacks in Wireless Sensor Networks Using Two-hops Neighbor Knowledge